Primary Driving Factors behind Vulnerability Assessment and Penetration Testing
Expansive peril and VAPT are fundamental to acknowledging a person's affiliation. The route followed by us ensures safety out of each highlighted reduction of perils — from the state of being to the human part to the activity of development.
Feasible safety begins with an away from of your shortcomings. We may assist in estimating your characteristics and risks for a huge collection of circumstances, from office safety to pioneer confirmation. Notwithstanding the way that we carry numerous long periods of expertise to the Vulnerability Assessment and Penetration Testing, yet our driving pros can similarly assist with finding assumed wellsprings of fresh perils.
Comprehensive Vulnerability Assessment and Penetration Testing
Predictable application upgrades and switches over to system app arrangements. Besides, it can address shortcoming and make you defenseless against an attack, whether or not you remain consciously awake with the most recent. For the security of your data, you ought to perpetually check all systems and contraptions to perceive shortcomings as they develop.
- Sets assigned shortcoming over the framework.
- Spots and sorts out shortcomings within the framework for remedy, considering the most unmistakable impact on the risk decline.
- Set solution exercises for shortcomings discovered in the examination; this regularly ensures a fix to be matched or advantage be contained.
How to Conduct Penetration Testing and Vulnerability Assessment
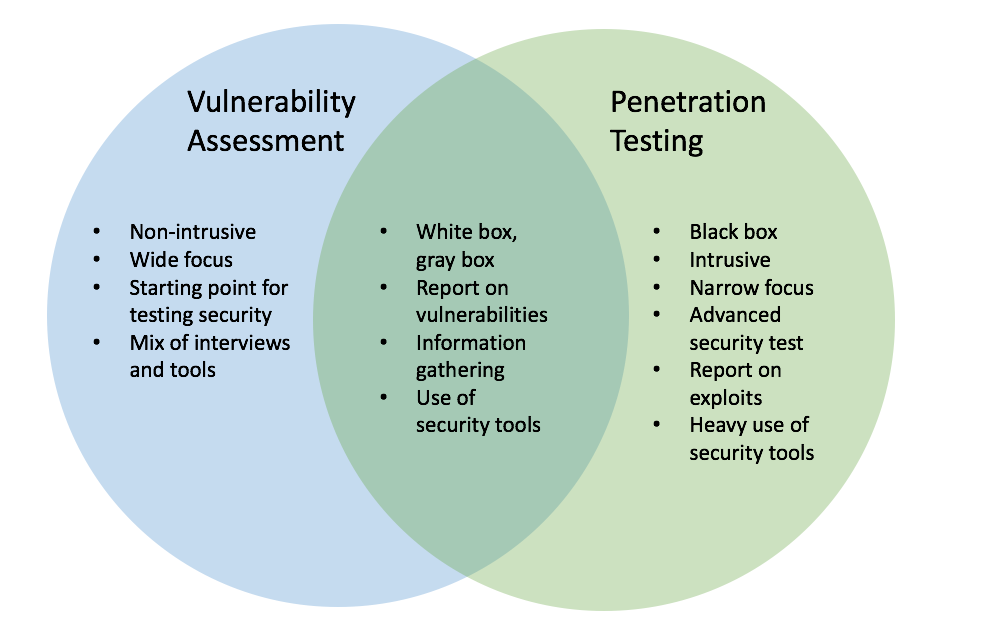
VAPT constitutes a couple of shortcoming checks. The tests set specific characteristics and are now and again joined for obtaining a more complex shortcoming assessment. To lay it out simply, Penetration Testing and Vulnerability Assessment conduct few particular tasks, generally speaking with separate outcomes, inside a comparative zone of center intrigue.
- The administration of Vulnerability Assessment gives a significant security evaluation of external and inner framework structure and applications, inside framework establishment, laborers and systems used by clients.
- The administration of Penetration Testing mishandles perceived shortcomings and shows the impact of those shortcomings to the extent of the productive intrusion circumstances.
Programmers are consistently keeping watch for chances to break into your framework. Guarding your framework information against their inquisitive eyes represents an extraordinary test. Security is a significant concern particularly when you are getting to unfamiliar organizations. Organizations venture some particular weakness appraisals every once in a while.
Surveying weaknesses and testing infiltration is a key segment in perceiving such weaknesses. The smallest proviso may allow the programmers to misuse openings causing break of agreement. It is significant for an organization to control the danger of data penetration.